tripleNAT
Участники форума-
Постов
13 -
Зарегистрирован
-
Посещение
Оборудование
-
Устройства
4G III
Посетители профиля
Блок последних пользователей отключён и не показывается другим пользователям.
Достижения tripleNAT

Пользователь (2/6)
1
Репутация
-
Какие подсети на устройствах? Причин может быть две: 1. Файрвол 2. Отсутствие маршрута в подсеть сервера (или клиента) Как правило, маршрут до подсети сервера добавлять вручную не требуется, если клиент получает локальный адрес из подсети сервера. Маршрут до сети клиента нужно прописывать руками. У вас точно нет доступа к сети сервера, а не клиента? Выкладывайте адреса подсетей (сервер, клиент), конфигурацию файрвол и настройки l2tp сервера, если не получится решить проблему.
-
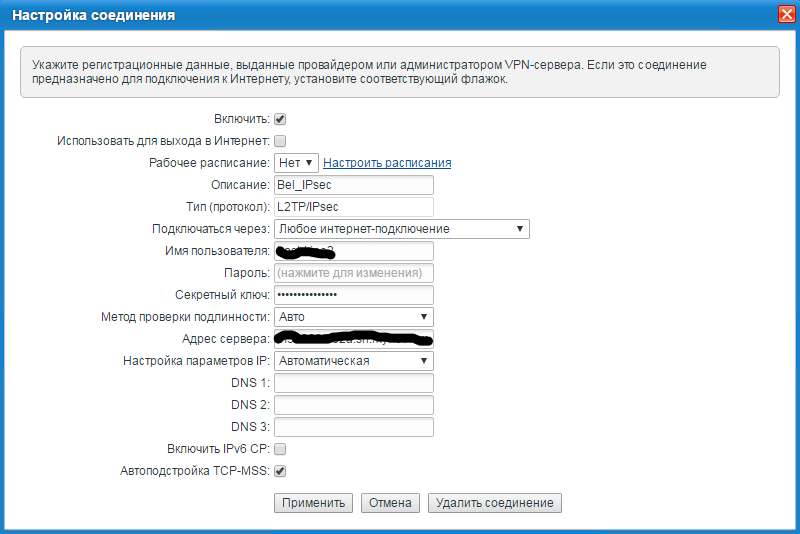
@Le ecureuil @vadimbn @r13 Друзья! Путем многочисленных проб и ошибок удалось разобраться с причиной проблемы подключения Keenetic 4G III rev.A к серверу L2TP over IPsec на Mikrotik. Создавая новые подключения и пробуя соединиться с различными серверами L2TP IPsec, получил множество успешных соединений вновь созданных подключений. Заподозрил неладное с PSK ключом (секретный ключ). Оказалось, однажды вписанный PSK ключ в подключении L2TP/IPsec Keenetic более не подлежит изменению! Впервые создав подключение, допустил ошибку в PSK ключе. В дальнейшем все мои правки оказались бесполезными, пока не создал новое подключение с правильным ключом. Замечу, что данная особенность "заморозки" значения переменной PSK ключа присутствует как в тестовой 2.09, так и в стабильной 2.08.
-
Согласен по поводу настроек Mikrotik. Так или иначе, используются дефолтные настройки peer. Сервер L2TP настроен как у вас, с указанием "использовать IPsec" и указанием IP secret. В proposals IPsec тоже самое. С другими устройствами все работает. Не подключается только Keenetic 4G III rev. A с любой прошивкой. @Le ecureuil Проверял-перепроверял PSK в первую очередь!
-
Обновился на отладочную 2.09. Логи на Keenetic и Mikrotik не изменились. Keenetic: Mar 14 10:34:51 ipsecStarting strongSwan 5.5.1 IPsec [starter]... Mar 14 10:34:51 ipsec00[DMN] Starting IKE charon daemon (strongSwan 5.5.1, Linux 3.4.113, mips) Mar 14 10:34:51 ipsec00[CFG] loading secrets Mar 14 10:34:51 ipsec00[CFG] loaded IKE secret for 192.168.1.100 5.228.74.226 Mar 14 10:34:51 ipsec00[CFG] starting systime check, interval: 10s Mar 14 10:34:51 ipsec00[LIB] loaded plugins: charon random nonce openssl hmac attr kernel-netlink socket-default stroke updown eap-mschapv2 eap-dynamic xauth-generic xauth-eap error-notify systime-fix unity Mar 14 10:34:51 ipsec05[CFG] received stroke: add connection 'L2TP0' Mar 14 10:34:51 ipsec05[CFG] added configuration 'L2TP0' Mar 14 10:34:51 ipsec07[CFG] received stroke: initiate 'L2TP0' Mar 14 10:34:51 ipsec07[IKE] sending DPD vendor ID Mar 14 10:34:51 ipsec07[IKE] sending FRAGMENTATION vendor ID Mar 14 10:34:51 ipsec07[IKE] sending NAT-T (RFC 3947) vendor ID Mar 14 10:34:51 ipsec07[IKE] sending draft-ietf-ipsec-nat-t-ike-02\n vendor ID Mar 14 10:34:51 ipsec07[IKE] initiating Main Mode IKE_SA L2TP0[1] to 5.228.74.226 Mar 14 10:34:51 ipsec09[IKE] received NAT-T (RFC 3947) vendor ID Mar 14 10:34:51 ipsec09[IKE] received DPD vendor ID Mar 14 10:34:51 ipsec09[IKE] received FRAGMENTATION vendor ID Mar 14 10:34:51 ipsec09[CFG] received proposals: IKE:AES_CBC=256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024/# Mar 14 10:34:51 ipsec09[CFG] configured proposals: IKE:AES_CBC=256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536/#, IKE:AES_CBC=128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536/#, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536/#, IKE:AES_CBC=256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024/#, IKE:AES_CBC=128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024/#, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024/# Mar 14 10:34:51 ipsec09[CFG] selected proposal: IKE:AES_CBC=256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024/# Mar 14 10:34:51 ipsec10[IKE] linked key for crypto map 'L2TP0' is not found, still searching Mar 14 10:34:51 ipsec10[IKE] local host is behind NAT, sending keep alives Mar 14 10:34:52 ndmCore::Server: started Session /var/run/ndm.core.socket. Mar 14 10:34:52 upnpHTTP listening on port 35555 Mar 14 10:34:52 upnpListening for NAT-PMP/PCP traffic on port 5351 Mar 14 10:34:57 ndmNetwork::Interface::WebCaller: calling http://192.168.1.1/api/device/information. Mar 14 10:34:59 ipsec06[IKE] sending retransmit 1 of request message ID 0, seq 3 Mar 14 10:35:01 ipsec07[IKE] received retransmit of response with ID 0, but next request already sent Mar 14 10:35:02 ndmNetwork::Interface::WebCaller: response: 200 (OK). Mar 14 10:35:08 ipsec11[IKE] sending retransmit 2 of request message ID 0, seq 3 Mar 14 10:35:11 ipsec16[IKE] received retransmit of response with ID 0, but next request already sent Mar 14 10:35:17 ipsec07[IKE] sending retransmit 3 of request message ID 0, seq 3 Mar 14 10:35:21 ipsec11[IKE] received retransmit of response with ID 0, but next request already sent Mar 14 10:35:28 ipsec16[IKE] sending retransmit 4 of request message ID 0, seq 3 Mar 14 10:35:31 ipsec05[IKE] received retransmit of response with ID 0, but next request already sent Mar 14 10:35:33 ndmDns::Manager: record "xxxx.mykeenetic.ru", address 78.47.125.180 deleted. Mar 14 10:35:33 ndmDns::Manager: added static record for "xxxx.mykeenetic.ru", address 78.47.125.180. Mar 14 10:35:40 ipsec12[IKE] sending retransmit 5 of request message ID 0, seq 3 Mar 14 10:35:41 ipsec14[IKE] received retransmit of response with ID 0, but next request already sent Mar 14 10:35:48 pptp[1826]Echo Reply received. Mar 14 10:35:53 ipsec09[IKE] sending retransmit 6 of request message ID 0, seq 3 Mar 14 10:36:07 ipsec06[IKE] sending retransmit 7 of request message ID 0, seq 3 Mar 14 10:36:23 ipsec14[IKE] sending retransmit 8 of request message ID 0, seq 3 Mar 14 10:36:40 ipsec12[IKE] giving up after 8 retransmits Mar 14 10:36:40 ndmIpSec::Configurator: remote peer of crypto map "L2TP0" is down. Mikrotik (последняя прошивка): 10:36:47 ipsec,info respond new phase 1 (Identity Protection): 5.228.74.226[500]<= >94.25.177.199[41915] 10:36:47 ipsec,error 94.25.177.199 parsing packet failed, possible cause: wrong password 10:36:55 ipsec,error 94.25.177.199 parsing packet failed, possible cause: wrong password 10:37:04 ipsec,error 94.25.177.199 parsing packet failed, possible cause: wrong password 10:37:14 ipsec,error 94.25.177.199 parsing packet failed, possible cause: wrong password 10:37:24 ipsec,error 94.25.177.199 parsing packet failed, possible cause: wrong password 10:37:36 ipsec,error 94.25.177.199 parsing packet failed, possible cause: wrong password 10:37:47 ipsec,error phase1 negotiation failed due to time up 5.228.74.226[4500]<= >94.25.177.199[25184] 7da7d05b60ca0696:e1bacd535782e6e7 Пароли точно верные. С ними подключаюсь с других устройств.
-
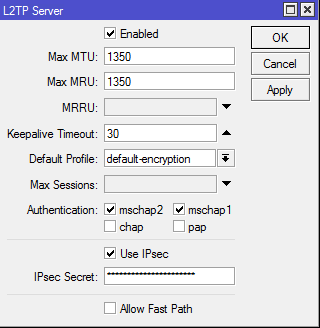
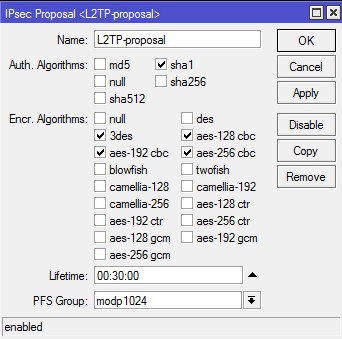
Спасибо за ответ. Вот настройки: /ip firewall filter add action=accept chain=input comment="Allow l2tp" dst-port=1701 protocol=udp add action=accept chain=input comment="Allow IPsec" dst-port=500,4500 \ protocol=udp /interface l2tp-server server set authentication=mschap1,mschap2 enabled=yes ipsec-secret=\ MMMMMM! max-mru=1350 max-mtu=1350 use-ipsec=yes /ip ipsec peer add address=0.0.0.0/0 dh-group=modp1536,modp1024 disabled=no enc-algorithm=\ aes-256,aes-128,3des exchange-mode=main-l2tp generate-policy=\ port-override passive=yes secret=MMMMMMM! add address=0.0.0.0/0 enc-algorithm=aes-256,aes-192,aes-128,3des \ exchange-mode=main-l2tp generate-policy=port-override secret=\ MMMMMMM! /ip ipsec policy set 0 proposal=L2TP-proposal /ip ipsec proposal set [ find default=yes ] auth-algorithms=sha512,sha256,sha1 disabled=no \ enc-algorithms=aes-256-cbc,aes-256-ctr,aes-128-cbc,aes-128-ctr,3des add enc-algorithms=aes-256-cbc,aes-192-cbc,aes-128-cbc,3des name=\ L2TP-proposal /ppp secret add local-address=192.168.XX.XX name=XXX password=XXXXX \ profile=default-encryption remote-address=192.168.XX.XX service=l2tp P.S. iPad'ы, iPhonе'ы и Windows PC подключаются к серверу mikrotik без проблем.
-
Добрый день! Спасибо команде zyxel за включение IPsec в прошивку бюджетных устройств. Был в числе запрашивавших этот функционал. При настройке L2TP IPsec клиента на keenetic 4G III для подключения к серверу mikrotik получаю: Feb 24 11:02:40ndm IpSec::Configurator: crypto map "L2TP0" active IKE SA: 0, active CHILD SA: 0. Feb 24 11:02:40ndm IpSec::Configurator: fallback peer is not defined for crypto map "L2TP0", retry. Feb 24 11:02:40ndm IpSec::Configurator: schedule reconnect for crypto map "L2TP0". Feb 24 11:02:40ndm Network::Interface::L2TP: "L2TP0": IPsec layer is down, shutdown L2TP layer. Feb 24 11:02:40ndm Network::Interface::PPP: "L2TP0": disabled connection. Feb 24 11:02:40ndm Network::Interface::PPP: "L2TP0": disabled connection. Feb 24 11:02:40ipsec 05[IKE] establishing IKE_SA failed, peer not responding Feb 24 11:02:41ndm Network::Interface::L2TP: "L2TP0": remote endpoint is resolved to "5.228.72.179". Feb 24 11:02:41ndm Network::Interface::L2TP: "L2TP0": local endpoint is resolved to "192.168.88.10". Feb 24 11:02:41ndm Network::Interface::L2TP: "L2TP0": updating IP secure configuration. Feb 24 11:02:41ndm IpSec::Manager: IP secure connection "L2TP0" and keys was deleted. Feb 24 11:02:41ndm IpSec::Manager: IP secure connection "L2TP0" was added. Feb 24 11:02:43ndm IpSec::Manager: create IPsec reconfiguration transaction... Feb 24 11:02:43ndm IpSec::Manager: IPsec reconfiguration transaction was created. Feb 24 11:02:43ndm IpSec::Configurator: start applying IPsec configuration. Feb 24 11:02:43ndm IpSec::Configurator: IPsec configuration applying is done. Feb 24 11:02:43ndm IpSec::Configurator: start reloading IKE keys task. Feb 24 11:02:43ipsec 15[CFG] rereading secrets Feb 24 11:02:43ipsec 15[CFG] loading secrets Feb 24 11:02:43ipsec 15[CFG] loaded IKE secret for 192.168.88.10 5.228.72.179 Feb 24 11:02:43ipsec 15[CFG] rereading ca certificates from '/tmp/ipsec/ipsec.d/cacerts' Feb 24 11:02:43ipsec 15[CFG] rereading aa certificates from '/tmp/ipsec/ipsec.d/aacerts' Feb 24 11:02:43ipsec 15[CFG] rereading ocsp signer certificates from '/tmp/ipsec/ipsec.d/ocspcerts' Feb 24 11:02:43ipsec 15[CFG] rereading attribute certificates from '/tmp/ipsec/ipsec.d/acerts' Feb 24 11:02:43ipsec 15[CFG] rereading crls from '/tmp/ipsec/ipsec.d/crls' Feb 24 11:02:43ndm IpSec::Configurator: reloading IKE keys task done. Feb 24 11:02:44ndm IpSec::Configurator: start reloading IPsec config task. Feb 24 11:02:44ipsec 12[CFG] received stroke: delete connection 'L2TP0' Feb 24 11:02:44ipsec 12[CFG] deleted connection 'L2TP0' Feb 24 11:02:44ipsec 00[DMN] signal of type SIGHUP received. Reloading configuration Feb 24 11:02:44ipsec 11[CFG] received stroke: add connection 'L2TP0' Feb 24 11:02:44ipsec 11[CFG] added configuration 'L2TP0' Feb 24 11:02:44ipsec 00[CFG] loaded 0 entries for attr plugin configuration Feb 24 11:02:44ndm IpSec::IpSecNetfilter: start reloading netfilter configuration... Feb 24 11:02:44ndm IpSec::IpSecNetfilter: netfilter configuration reloading is done. Feb 24 11:02:44ndm IpSec::Configurator: reloading IPsec config task done. Feb 24 11:02:45ndm IpSec::Configurator: crypto map "L2TP0" shutdown started. Feb 24 11:02:45ipsec 09[CFG] received stroke: unroute 'L2TP0' Feb 24 11:02:45ipsec 06[CFG] received stroke: terminate 'L2TP0{*}' Feb 24 11:02:45ipsec 06[CFG] no CHILD_SA named 'L2TP0' found Feb 24 11:02:46ipsec 07[CFG] received stroke: terminate 'L2TP0[*]' Feb 24 11:02:46ipsec 07[CFG] no IKE_SA named 'L2TP0' found Feb 24 11:02:46ndm IpSec::Configurator: crypto map "L2TP0" shutdown complete. Feb 24 11:02:46ipsec 16[CFG] received stroke: initiate 'L2TP0' Feb 24 11:02:46ndm IpSec::Configurator: crypto map "L2TP0" initialized. Feb 24 11:02:46ipsec 12[IKE] sending DPD vendor ID Feb 24 11:02:46ipsec 12[IKE] sending FRAGMENTATION vendor ID Feb 24 11:02:46ipsec 12[IKE] sending NAT-T (RFC 3947) vendor ID Feb 24 11:02:46ipsec 12[IKE] sending draft-ietf-ipsec-nat-t-ike-02\n vendor ID Feb 24 11:02:46ipsec 12[IKE] initiating Main Mode IKE_SA L2TP0[328] to 5.228.72.179 Feb 24 11:02:47ipsec 11[IKE] received NAT-T (RFC 3947) vendor ID Feb 24 11:02:47ipsec 11[IKE] received DPD vendor ID Feb 24 11:02:47ipsec 11[IKE] received FRAGMENTATION vendor ID Feb 24 11:02:47ipsec 11[CFG] received proposals: IKE:AES_CBC=256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536/# Feb 24 11:02:47ipsec 11[CFG] configured proposals: IKE:AES_CBC=256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536/#, IKE:AES_CBC=128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536/#, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536/#, IKE:AES_CBC=256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024/#, IKE:AES_CBC=128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024/#, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024/# Feb 24 11:02:47ipsec 11[CFG] selected proposal: IKE:AES_CBC=256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536/# Feb 24 11:02:47ipsec 10[IKE] linked key for crypto map 'L2TP0' is not found, still searching Feb 24 11:02:47ipsec 10[IKE] local host is behind NAT, sending keep alives Feb 24 11:02:55ipsec 08[IKE] sending retransmit 1 of request message ID 0, seq 3 Feb 24 11:02:57ipsec 14[IKE] received retransmit of response with ID 0, but next request already sent Feb 24 11:03:04ipsec 09[IKE] sending retransmit 2 of request message ID 0, seq 3 Feb 24 11:03:07ipsec 13[IKE] received retransmit of response with ID 0, but next request already sent Feb 24 11:03:14ipsec 15[IKE] sending retransmit 3 of request message ID 0, seq 3 Feb 24 11:03:17ipsec 11[IKE] received retransmit of response with ID 0, but next request already sent Feb 24 11:03:25ipsec 05[IKE] sending retransmit 4 of request message ID 0, seq 3 Feb 24 11:03:27ipsec 07[IKE] received retransmit of response with ID 0, but next request already sent Feb 24 11:03:36ipsec 11[IKE] sending retransmit 5 of request message ID 0, seq 3 Feb 24 11:03:37ipsec 09[IKE] received retransmit of response with ID 0, but next request already sent Feb 24 11:03:49ipsec 14[IKE] sending retransmit 6 of request message ID 0, seq 3 Feb 24 11:04:03ipsec 06[IKE] sending retransmit 7 of request message ID 0, seq 3 Feb 24 11:04:19ipsec 06[IKE] sending retransmit 8 of request message ID 0, seq 3 Feb 24 11:04:36ipsec 10[IKE] giving up after 8 retransmits Feb 24 11:04:36ndm IpSec::Configurator: remote peer of crypto map "L2TP0" is down.