KVA KVA
Участники форума-
Постов
7 -
Зарегистрирован
-
Посещение
Тип контента
Профили
Форумы
Галерея
Загрузки
Блоги
События
Весь контент KVA KVA
-
Нашел сообщение с подобной проблемой. Сделал как в этом примере. Отключил клиентское приложение включил сервер, соединилось. Но вопрос открыт, как запустить и клиент и сервер одновременно.
- 1 ответ
-
- ikev2
- strongswan
-
(и ещё 1 )
C тегом:
-
Добрый день, настроил ikev2 сервер на своем роутере (kn-1011) по примеру с офф сайта кинетика (https://help.keenetic.com/hc/ru/articles/360017022999-VPN-сервер-IKEv2). При подключении к нему через strongswan с андроид устройства (делал так же как на сайте https://help.keenetic.com/hc/ru/articles/8866287233180-Подключение-к-VPN-серверу-IKEv2-из-Android) ссылается на ошибку авторизации. В логах посмотрел ссылается на какой-то сертификат, которого быть то и не должно. Во встроенном клиенте Windows тоже нет соединения. На всякий случай, по окружению: провайдер не блокирует vpn т.к. этот роутер уже является клиентом у другого сервера все прекрасно работает на том же протоколе. keendns подключен, пробовал по имени хоста соединить и по прямому ip, результат тот же. Прилагаю лог из strongswan Jan 28 10:12:23 00[DMN] +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ Jan 28 10:12:23 00[DMN] Starting IKE service (strongSwan 5.9.14, Android 14 - UP1A.231005.007.S721BXXS3AXL1/2025-01-01, SM-S721B - samsung/r12sxxx/samsung, Linux 6.1.75-android14-11, aarch64, org.strongswan.android) Jan 28 10:12:23 00[LIB] providers loaded by OpenSSL: default legacy Jan 28 10:12:23 00[LIB] loaded plugins: androidbridge charon android-log socket-default openssl nonce pkcs1 pem x509 xcbc kdf revocation eap-identity eap-mschapv2 eap-md5 eap-gtc eap-tls Jan 28 10:12:23 00[JOB] spawning 16 worker threads Jan 28 10:12:23 07[IKE] initiating IKE_SA android[4] to IP моего хоста Jan 28 10:12:23 07[ENC] generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ] Jan 28 10:12:23 07[NET] sending packet: from 192.100.0.111[41498] to IP моего хоста[500] (948 bytes) Jan 28 10:12:23 08[NET] received packet: from IP моего хоста[500] to 192.100.0.111[41498] (38 bytes) Jan 28 10:12:23 08[ENC] parsed IKE_SA_INIT response 0 [ N(INVAL_KE) ] Jan 28 10:12:23 08[IKE] peer didn't accept DH group ECP_256, it requested MODP_2048 Jan 28 10:12:23 08[IKE] initiating IKE_SA android[4] to IP моего хоста Jan 28 10:12:23 08[ENC] generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ] Jan 28 10:12:23 08[NET] sending packet: from 192.100.0.111[41498] to IP моего хоста[500] (1140 bytes) Jan 28 10:12:23 09[NET] received packet: from IP моего хоста[500] to 192.100.0.111[41498] (517 bytes) Jan 28 10:12:23 09[ENC] parsed IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(HASH_ALG) N(CHDLESS_SUP) N(MULT_AUTH) ] Jan 28 10:12:23 09[CFG] selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 Jan 28 10:12:23 09[IKE] local host is behind NAT, sending keep alives Jan 28 10:12:23 09[IKE] remote host is behind NAT Jan 28 10:12:23 09[IKE] received cert request for "CN=VPN root CA" Jan 28 10:12:23 09[IKE] received 1 cert requests for an unknown ca Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Certainly, CN=Certainly Root R1" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Internet Security Research Group, CN=ISRG Root X1" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Internet Security Research Group, CN=ISRG Root X2" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=IdenTrust, CN=IdenTrust Public Sector Root CA 1" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert High Assurance EV Root CA" Jan 28 10:12:23 09[IKE] sending cert request for "OU=GlobalSign Root CA - R3, O=GlobalSign, CN=GlobalSign" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=DigiCert, Inc., CN=DigiCert TLS ECC P384 Root G5" Jan 28 10:12:23 09[IKE] sending cert request for "C=FR, O=Dhimyotis, OU=0002 48146308100036, CN=Certigna Root CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=FI, O=Telia Finland Oyj, CN=Telia Root CA v2" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=CommScope, CN=CommScope Public Trust ECC Root-01" Jan 28 10:12:23 09[IKE] sending cert request for "CN=Atos TrustedRoot Root CA ECC TLS 2021, O=Atos, C=DE" Jan 28 10:12:23 09[IKE] sending cert request for "C=IT, L=Milan, O=Actalis S.p.A./03358520967, CN=Actalis Authentication Root CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=PL, O=Asseco Data Systems S.A., OU=Certum Certification Authority, CN=Certum EC-384 CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=IdenTrust, CN=IdenTrust Commercial Root CA 1" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, ST=Texas, L=Houston, O=SSL Corporation, CN=SSL.com Root Certification Authority RSA" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Google Trust Services LLC, CN=GTS Root R3" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Assured ID Root CA" Jan 28 10:12:23 09[IKE] sending cert request for "CN=Atos TrustedRoot Root CA RSA TLS 2021, O=Atos, C=DE" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Starfield Technologies, Inc., OU=Starfield Class 2 Certification Authority" Jan 28 10:12:23 09[IKE] sending cert request for "C=GR, O=Hellenic Academic and Research Institutions CA, CN=HARICA TLS RSA Root CA 2021" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, ST=Illinois, L=Chicago, O=Trustwave Holdings, Inc., CN=Trustwave Global ECC P384 Certification Authority" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Google Trust Services LLC, CN=GTS Root R2" Jan 28 10:12:23 09[IKE] sending cert request for "C=TW, O=Chunghwa Telecom Co., Ltd., OU=ePKI Root Certification Authority" Jan 28 10:12:23 09[IKE] sending cert request for "C=TW, O=Chunghwa Telecom Co., Ltd., CN=HiPKI Root CA - G1" Jan 28 10:12:23 09[IKE] sending cert request for "C=RO, O=certSIGN, OU=certSIGN ROOT CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=GR, L=Athens, O=Hellenic Academic and Research Institutions Cert. Authority, CN=Hellenic Academic and Research Institutions RootCA 2015" Jan 28 10:12:23 09[IKE] sending cert request for "C=FR, O=Dhimyotis, CN=Certigna" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Microsoft Corporation, CN=Microsoft ECC Root Certificate Authority 2017" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, ST=Illinois, L=Chicago, O=Trustwave Holdings, Inc., CN=Trustwave Global ECC P256 Certification Authority" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=CommScope, CN=CommScope Public Trust RSA Root-02" Jan 28 10:12:23 09[IKE] sending cert request for "C=HK, ST=Hong Kong, L=Hong Kong, O=Hongkong Post, CN=Hongkong Post Root CA 3" Jan 28 10:12:23 09[IKE] sending cert request for "C=CN, O=BEIJING CERTIFICATE AUTHORITY, CN=BJCA Global Root CA1" Jan 28 10:12:23 09[IKE] sending cert request for "C=AT, O=e-commerce monitoring GmbH, CN=GLOBALTRUST 2020" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Certainly, CN=Certainly Root E1" Jan 28 10:12:23 09[IKE] sending cert request for "C=NO, O=Buypass AS-983163327, CN=Buypass Class 2 Root CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Amazon, CN=Amazon Root CA 1" Jan 28 10:12:23 09[IKE] sending cert request for "C=SK, L=Bratislava, O=Disig a.s., CN=CA Disig Root R2" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Microsoft Corporation, CN=Microsoft RSA Root Certificate Authority 2017" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Trusted Root G4" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=SSL Corporation, CN=SSL.com TLS RSA Root CA 2022" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, ST=New Jersey, L=Jersey City, O=The USERTRUST Network, CN=USERTrust RSA Certification Authority" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root G2" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Google Trust Services LLC, CN=GTS Root R4" Jan 28 10:12:23 09[IKE] sending cert request for "C=DE, O=D-Trust GmbH, CN=D-TRUST BR Root CA 1 2020" Jan 28 10:12:23 09[IKE] sending cert request for "C=BE, O=GlobalSign nv-sa, CN=GlobalSign Root R46" Jan 28 10:12:23 09[IKE] sending cert request for "C=CH, O=SwissSign AG, CN=SwissSign Gold CA - G2" Jan 28 10:12:23 09[IKE] sending cert request for "C=CN, O=GUANG DONG CERTIFICATE AUTHORITY CO.,LTD., CN=GDCA TrustAUTH R5 ROOT" Jan 28 10:12:23 09[IKE] sending cert request for "C=CN, O=TrustAsia Technologies, Inc., CN=TrustAsia Global Root CA G4" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=SecureTrust Corporation, CN=SecureTrust CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=BE, O=GlobalSign nv-sa, OU=Root CA, CN=GlobalSign Root CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 3" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root CA" Jan 28 10:12:23 09[IKE] sending cert request for "CN=ACCVRAIZ1, OU=PKIACCV, O=ACCV, C=ES" Jan 28 10:12:23 09[IKE] sending cert request for "C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 2 G3" Jan 28 10:12:23 09[IKE] sending cert request for "C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 2" Jan 28 10:12:23 09[IKE] sending cert request for "C=TW, O=TAIWAN-CA, OU=Root CA, CN=TWCA Global Root CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=GB, ST=Greater Manchester, L=Salford, O=COMODO CA Limited, CN=COMODO ECC Certification Authority" Jan 28 10:12:23 09[IKE] sending cert request for "C=HU, L=Budapest, O=Microsec Ltd., CN=Microsec e-Szigno Root CA 2009, E=info@e-szigno.hu" Jan 28 10:12:23 09[IKE] sending cert request for "C=CH, O=WISeKey, OU=OISTE Foundation Endorsed, CN=OISTE WISeKey Global Root GC CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=CN, O=iTrusChina Co.,Ltd., CN=vTrus ECC Root CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=AffirmTrust, CN=AffirmTrust Commercial" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Google Trust Services LLC, CN=GTS Root R1" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, ST=Arizona, L=Scottsdale, O=Starfield Technologies, Inc., CN=Starfield Services Root Certificate Authority - G2" Jan 28 10:12:23 09[IKE] sending cert request for "serialNumber=G63287510, C=ES, O=ANF Autoridad de Certificacion, OU=ANF CA Raiz, CN=ANF Secure Server Root CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=DE, O=D-Trust GmbH, CN=D-TRUST Root Class 3 CA 2 EV 2009" Jan 28 10:12:23 09[IKE] sending cert request for "C=ES, CN=Autoridad de Certificacion Firmaprofesional CIF A62634068" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, ST=Texas, L=Houston, O=SSL Corporation, CN=SSL.com EV Root Certification Authority ECC" Jan 28 10:12:23 09[IKE] sending cert request for "OU=GlobalSign Root CA - R6, O=GlobalSign, CN=GlobalSign" Jan 28 10:12:23 09[IKE] sending cert request for "C=HU, L=Budapest, O=Microsec Ltd., 55:04:61=VATHU-23584497, CN=e-Szigno Root CA 2017" Jan 28 10:12:23 09[IKE] sending cert request for "CN=VPN root CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=GR, O=Hellenic Academic and Research Institutions CA, CN=HARICA TLS ECC Root CA 2021" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Entrust, Inc., OU=www.entrust.net/CPS is incorporated by reference, OU=(c) 2006 Entrust, Inc., CN=Entrust Root Certification Authority" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, OU=emSign PKI, O=eMudhra Inc, CN=emSign Root CA - C1" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, ST=Texas, L=Houston, O=SSL Corporation, CN=SSL.com EV Root Certification Authority RSA R2" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=CommScope, CN=CommScope Public Trust ECC Root-02" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Entrust, Inc., OU=See www.entrust.net/legal-terms, OU=(c) 2015 Entrust, Inc. - for authorized use only, CN=Entrust Root Certification Authority - G4" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, ST=Arizona, L=Scottsdale, O=GoDaddy.com, Inc., CN=Go Daddy Root Certificate Authority - G2" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=CommScope, CN=CommScope Public Trust RSA Root-01" Jan 28 10:12:23 09[IKE] sending cert request for "C=CN, O=TrustAsia Technologies, Inc., CN=TrustAsia Global Root CA G3" Jan 28 10:12:23 09[IKE] sending cert request for "C=GB, O=Sectigo Limited, CN=Sectigo Public Server Authentication Root R46" Jan 28 10:12:23 09[IKE] sending cert request for "C=CH, O=WISeKey, OU=OISTE Foundation Endorsed, CN=OISTE WISeKey Global Root GB CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, OU=emSign PKI, O=eMudhra Inc, CN=emSign ECC Root CA - C3" Jan 28 10:12:23 09[IKE] sending cert request for "C=PL, O=Asseco Data Systems S.A., OU=Certum Certification Authority, CN=Certum Trusted Root CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=ES, O=IZENPE S.A., CN=Izenpe.com" Jan 28 10:12:23 09[IKE] sending cert request for "CN=Atos TrustedRoot 2011, O=Atos, C=DE" Jan 28 10:12:23 09[IKE] sending cert request for "C=IN, OU=emSign PKI, O=eMudhra Technologies Limited, CN=emSign Root CA - G1" Jan 28 10:12:23 09[IKE] sending cert request for "C=TR, L=Gebze - Kocaeli, O=Turkiye Bilimsel ve Teknolojik Arastirma Kurumu - TUBITAK, OU=Kamu Sertifikasyon Merkezi - Kamu SM, CN=TUBITAK Kamu SM SSL Kok Sertifikasi - Surum 1" Jan 28 10:12:23 09[IKE] sending cert request for "C=ES, O=FNMT-RCM, OU=AC RAIZ FNMT-RCM" Jan 28 10:12:23 09[IKE] sending cert request for "C=DE, O=T-Systems Enterprise Services GmbH, OU=T-Systems Trust Center, CN=T-TeleSec GlobalRoot Class 2" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Assured ID Root G3" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Assured ID Root G2" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, ST=Arizona, L=Scottsdale, O=Starfield Technologies, Inc., CN=Starfield Root Certificate Authority - G2" Jan 28 10:12:23 09[IKE] sending cert request for "C=GB, ST=Greater Manchester, L=Salford, O=Comodo CA Limited, CN=AAA Certificate Services" Jan 28 10:12:23 09[IKE] sending cert request for "C=TW, O=TAIWAN-CA, OU=Root CA, CN=TWCA Root Certification Authority" Jan 28 10:12:23 09[IKE] sending cert request for "C=HU, L=Budapest, O=NetLock Kft., OU=Tan??s??tv??nykiad??k (Certification Services), CN=NetLock Arany (Class Gold) F??tan??s??tv??ny" Jan 28 10:12:23 09[IKE] sending cert request for "C=GB, O=Sectigo Limited, CN=Sectigo Public Server Authentication Root E46" Jan 28 10:12:23 09[IKE] sending cert request for "C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 1 G3" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Amazon, CN=Amazon Root CA 2" Jan 28 10:12:23 09[IKE] sending cert request for "OU=GlobalSign ECC Root CA - R4, O=GlobalSign, CN=GlobalSign" Jan 28 10:12:23 09[IKE] sending cert request for "C=JP, O=SECOM Trust Systems CO.,LTD., CN=Security Communication RootCA3" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root G3" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=The Go Daddy Group, Inc., OU=Go Daddy Class 2 Certification Authority" Jan 28 10:12:23 09[IKE] sending cert request for "C=CN, O=iTrusChina Co.,Ltd., CN=vTrus Root CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=PL, O=Unizeto Technologies S.A., OU=Certum Certification Authority, CN=Certum Trusted Network CA 2" Jan 28 10:12:23 09[IKE] sending cert request for "C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 3 G3" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=DigiCert, Inc., CN=DigiCert TLS RSA4096 Root G5" Jan 28 10:12:23 09[IKE] sending cert request for "C=JP, O=Japan Certification Services, Inc., CN=SecureSign RootCA11" Jan 28 10:12:23 09[IKE] sending cert request for "C=CN, O=UniTrust, CN=UCA Extended Validation Root" Jan 28 10:12:23 09[IKE] sending cert request for "C=TN, O=Agence Nationale de Certification Electronique, CN=TunTrust Root CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=DE, O=D-Trust GmbH, CN=D-TRUST EV Root CA 1 2020" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=SecureTrust Corporation, CN=Secure Global CA" Jan 28 10:12:23 09[IKE] sending cert request for "O=Entrust.net, OU=www.entrust.net/CPS_2048 incorp. by ref. (limits liab.), OU=(c) 1999 Entrust.net Limited, CN=Entrust.net Certification Authority (2048)" Jan 28 10:12:23 09[IKE] sending cert request for "C=GB, ST=Greater Manchester, L=Salford, O=COMODO CA Limited, CN=COMODO RSA Certification Authority" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Entrust, Inc., OU=See www.entrust.net/legal-terms, OU=(c) 2009 Entrust, Inc. - for authorized use only, CN=Entrust Root Certification Authority - G2" Jan 28 10:12:23 09[IKE] sending cert request for "C=DE, O=T-Systems Enterprise Services GmbH, OU=T-Systems Trust Center, CN=T-TeleSec GlobalRoot Class 3" Jan 28 10:12:23 09[IKE] sending cert request for "C=JP, O=SECOM Trust Systems CO.,LTD., OU=Security Communication RootCA2" Jan 28 10:12:23 09[IKE] sending cert request for "C=PL, O=Krajowa Izba Rozliczeniowa S.A., CN=SZAFIR ROOT CA2" Jan 28 10:12:23 09[IKE] sending cert request for "C=GR, L=Athens, O=Hellenic Academic and Research Institutions Cert. Authority, CN=Hellenic Academic and Research Institutions ECC RootCA 2015" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=AffirmTrust, CN=AffirmTrust Premium ECC" Jan 28 10:12:23 09[IKE] sending cert request for "C=GB, ST=Greater Manchester, L=Salford, O=COMODO CA Limited, CN=COMODO Certification Authority" Jan 28 10:12:23 09[IKE] sending cert request for "C=NO, O=Buypass AS-983163327, CN=Buypass Class 3 Root CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=AffirmTrust, CN=AffirmTrust Premium" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, OU=www.xrampsecurity.com, O=XRamp Security Services Inc, CN=XRamp Global Certification Authority" Jan 28 10:12:23 09[IKE] sending cert request for "C=BE, O=GlobalSign nv-sa, CN=GlobalSign Root E46" Jan 28 10:12:23 09[IKE] sending cert request for "O=TeliaSonera, CN=TeliaSonera Root CA v1" Jan 28 10:12:23 09[IKE] sending cert request for "C=IE, O=Baltimore, OU=CyberTrust, CN=Baltimore CyberTrust Root" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, ST=Texas, L=Houston, O=SSL Corporation, CN=SSL.com Root Certification Authority ECC" Jan 28 10:12:23 09[IKE] sending cert request for "C=ES, O=FNMT-RCM, OU=Ceres, 55:04:61=VATES-Q2826004J, CN=AC RAIZ FNMT-RCM SERVIDORES SEGUROS" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Amazon, CN=Amazon Root CA 4" Jan 28 10:12:23 09[IKE] sending cert request for "OU=GlobalSign ECC Root CA - R5, O=GlobalSign, CN=GlobalSign" Jan 28 10:12:23 09[IKE] sending cert request for "C=JP, O=SECOM Trust Systems CO.,LTD., CN=Security Communication ECC RootCA1" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, ST=New Jersey, L=Jersey City, O=The USERTRUST Network, CN=USERTrust ECC Certification Authority" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Entrust, Inc., OU=See www.entrust.net/legal-terms, OU=(c) 2012 Entrust, Inc. - for authorized use only, CN=Entrust Root Certification Authority - EC1" Jan 28 10:12:23 09[IKE] sending cert request for "C=CN, O=BEIJING CERTIFICATE AUTHORITY, CN=BJCA Global Root CA2" Jan 28 10:12:23 09[IKE] sending cert request for "C=CH, O=SwissSign AG, CN=SwissSign Silver CA - G2" Jan 28 10:12:23 09[IKE] sending cert request for "C=DE, O=D-Trust GmbH, CN=D-TRUST Root Class 3 CA 2 2009" Jan 28 10:12:23 09[IKE] sending cert request for "C=RO, O=CERTSIGN SA, OU=certSIGN ROOT CA G2" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=Amazon, CN=Amazon Root CA 3" Jan 28 10:12:23 09[IKE] sending cert request for "C=IN, OU=emSign PKI, O=eMudhra Technologies Limited, CN=emSign ECC Root CA - G3" Jan 28 10:12:23 09[IKE] sending cert request for "C=CN, O=UniTrust, CN=UCA Global G2 Root" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, ST=Illinois, L=Chicago, O=Trustwave Holdings, Inc., CN=Trustwave Global Certification Authority" Jan 28 10:12:23 09[IKE] sending cert request for "C=CN, O=China Financial Certification Authority, CN=CFCA EV ROOT" Jan 28 10:12:23 09[IKE] sending cert request for "C=PL, O=Unizeto Technologies S.A., OU=Certum Certification Authority, CN=Certum Trusted Network CA" Jan 28 10:12:23 09[IKE] sending cert request for "C=KR, O=NAVER BUSINESS PLATFORM Corp., CN=NAVER Global Root Certification Authority" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=SSL Corporation, CN=SSL.com TLS ECC Root CA 2022" Jan 28 10:12:23 09[IKE] sending cert request for "C=US, O=AffirmTrust, CN=AffirmTrust Networking" Jan 28 10:12:23 09[IKE] establishing CHILD_SA android{4} Jan 28 10:12:23 09[ENC] generating IKE_AUTH request 1 [ IDi N(INIT_CONTACT) CERTREQ CPRQ(ADDR ADDR6 DNS DNS6) SA TSi TSr N(MOBIKE_SUP) N(NO_ADD_ADDR) N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ] Jan 28 10:12:23 09[ENC] splitting IKE message (3344 bytes) into 3 fragments Jan 28 10:12:23 09[ENC] generating IKE_AUTH request 1 [ EF(1/3) ] Jan 28 10:12:23 09[ENC] generating IKE_AUTH request 1 [ EF(2/3) ] Jan 28 10:12:23 09[ENC] generating IKE_AUTH request 1 [ EF(3/3) ] Jan 28 10:12:23 09[NET] sending packet: from 192.100.0.111[53627] to IP моего хоста[4500] (1364 bytes) Jan 28 10:12:23 09[NET] sending packet: from 192.100.0.111[53627] to IP моего хоста[4500] (1364 bytes) Jan 28 10:12:23 09[NET] sending packet: from 192.100.0.111[53627] to IP моего хоста[4500] (772 bytes) Jan 28 10:12:24 12[NET] received packet: from IP моего хоста[4500] to 192.100.0.111[53627] (1236 bytes) Jan 28 10:12:24 12[ENC] parsed IKE_AUTH response 1 [ EF(1/2) ] Jan 28 10:12:24 12[ENC] received fragment #1 of 2, waiting for complete IKE message Jan 28 10:12:24 13[NET] received packet: from IP моего хоста[4500] to 192.100.0.111[53627] (548 bytes) Jan 28 10:12:24 13[ENC] parsed IKE_AUTH response 1 [ EF(2/2) ] Jan 28 10:12:24 13[ENC] received fragment #2 of 2, reassembled fragmented IKE message (1696 bytes) Jan 28 10:12:24 13[ENC] parsed IKE_AUTH response 1 [ IDr CERT AUTH EAP/REQ/ID ] Jan 28 10:12:24 13[IKE] received end entity cert "CN=ИМЯ моего хоста" Jan 28 10:12:24 13[CFG] using certificate "CN=ИМЯ моего хоста" Jan 28 10:12:24 13[CFG] no issuer certificate found for "CN=ИМЯ моего хоста" Jan 28 10:12:24 13[CFG] issuer is "C=US, O=Let's Encrypt, CN=R11" Jan 28 10:12:24 13[IKE] no trusted RSA public key found for 'ИМЯ моего хоста' Jan 28 10:12:24 13[ENC] generating INFORMATIONAL request 2 [ N(AUTH_FAILED) ] Jan 28 10:12:24 13[NET] sending packet: from 192.100.0.111[53627] to IP моего хоста[4500] (80 bytes)
- 1 ответ
-
- ikev2
- strongswan
-
(и ещё 1 )
C тегом:
-
Снова здравствуйте, это не оказалось решением проблемы. На основное подключение роутер не возвращается.
-
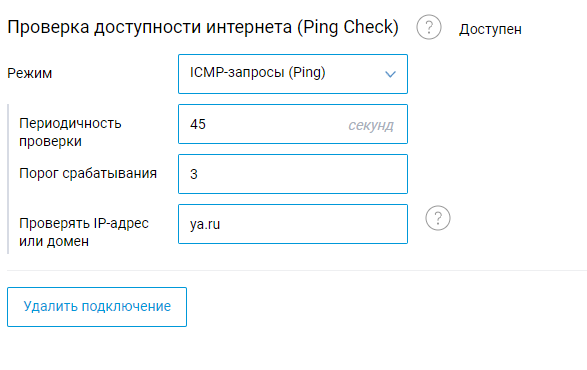
Вероятно, я нашел причину своей проблемы. Слишком малый интервал PingCheck для подтверждения работоспособности канала. Первоначальные настройки предполагали 3 попытки каждые 15 секунд до ya.ru, но мой провайдер попадал между этим интервалом и роутер не мог подтвердить связь. Я увеличил интервал до 45 секунд и он автоматически перешел на основной канал. Вот и вся беда. Буду наблюдать за результатом, но кажется это решение моей проблемы.
-
Здравствуйте, настроил резервный канал на роутере Keenetik giga (версия 4.0.7). Один провод приходит от провайдера напрямую подключение по pptp, второй (резервный) vdsl линия в ней стоит роутер от ростелекома и мой кинетик стоит в подсети получает ip по dhcp (по сути переходник) также логин в их сети по pptp. Суть проблемы при переходе роутера на работу от резервного канала все отрабатывает штатно он переключается на ростелеком. При возвращении линка на основном провайдере роутер выдает ошибку о том что не удалось соединиться с сервером. При перезагрузке роутера (перезагрузка порта не помогает) он автоматически использует основной канал. Предполагаю что дело в сессиях у провайдера но, ради меня одного никакие настройки менять не будут, подскажите как можно решить эту проблему или автоматизировать перезагрузку?